Cybersecurity Shared Responsibility Model
Overview
Our Cybersecurity Shared Responsibility Model is designed in the methods we have built for the Istari Digital application within Amazon Web Services (AWS) and ensures we have a comprehensive approach to security and compliance. The below Shared Responsibility Model is divided into three control categories:
- Inherited (Istari Digital or AWS)
- Customer
- Hybrid
The controls below serve as an initiating point for shared responsibility discussions and may need to be adjusted based on the customer’s cybersecurity requirements. Istari Digital will consistently review these controls and if the status of the Shared Responsibility changes, the customer will be notified.
The Cybersecurity Shared Responsibility Model control answers are provided under the Cybersecurity Maturity Model Certification (CMMC) Level 2 process for processing Controlled Unclassified Information (CUI) and International Traffic in Arms Regulations (ITAR) data. There are 110 applicable controls under CMMC Level 2. Reference Figure 1 below for a breakout of control inheritance percentages.
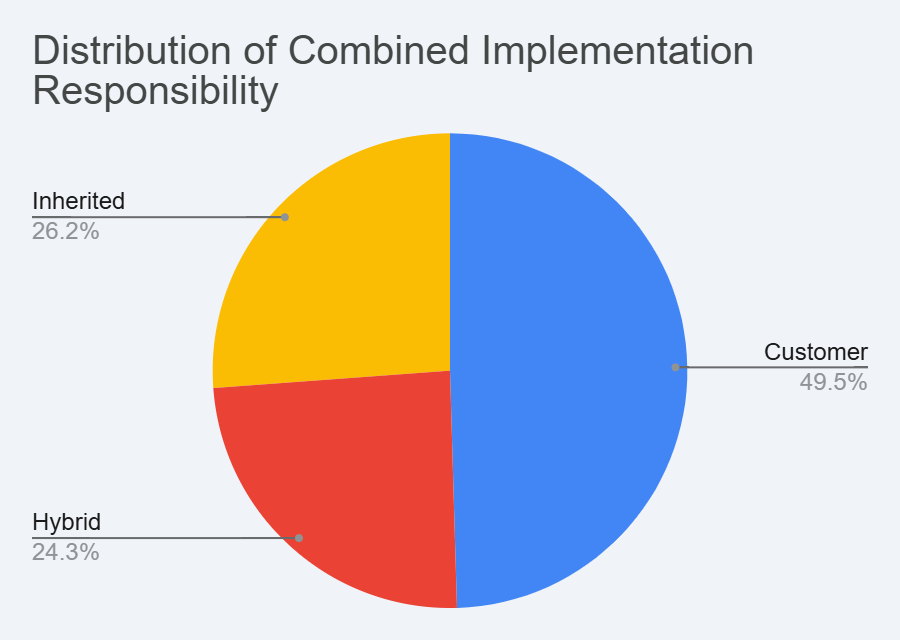
Figure 1 – Shared Responsibility Model Percentage Breakdown
Istari Digital & AWS Inherited Controls
These are security controls that customers inherit from the application and from our AWS deployments. Inherited controls include infrastructure and foundational services such as physical security, environmental controls, and the security of the hardware and software that powers cloud services. Customers benefit from these controls without direct action, as they are embedded in the service provided by Istari Digital.
| Domain | Control | Control Title | Implementation Responsibility | Implementation Narrative |
|---|---|---|---|---|
| AC | AC.L2-3.1.9 | Privacy & Security Notices | Istari Digital | The Istari Digital Platform provides appropriate banners consistent with the requirements of this control. |
| CM | CM.L2-3.4.1 | System Baselining | Istari Digital | The Istari Digital Platform contains multiple types of systems including Virtual Machines (VM), containerized systems, and other software/tools required for platform operations. |
| CM | CM.L2-3.4.2 | Security Configuration Enforcement | Istari Digital | Istari Digital maintains configuration documentation and security scans of our systems. If alternative software or images are used consistent with the customer's requirements, additional configuration may be required for functionality or security. |
| IA | IA.L2-3.5.5 | Identifier Reuse | Istari Digital | The Istari Digital Platform requires users and processes within its boundary to have unique identifiers. |
| IA | IA.L2-3.5.10 | Cryptographically Protected Passwords | Istari Digital | The Istari Digital Platform obscures passwords. |
| IA | IA.L2-3.5.11 | Obscure Feedback | Istari Digital | The Istari Digital Platform obscures feedback for unauthorized login attempts. |
| MA | MA.L2-3.7.1 | Perform Maintenance | AWS | Inherited by AWS. |
| MA | MA.L2-3.7.2 | System Maintenance Control | AWS | |
| MA | MA.L2-3.7.3 | Equipment Sanitization | AWS | |
| MA | MA.L2-3.7.4 | Media Inspection | AWS | |
| MA | MA.L2-3.7.5 | Nonlocal Maintenance | AWS | |
| MA | MA.L2-3.7.6 | Maintenance Personnel | AWS | |
| MP | MP.L2-3.8.1 | Media Protection | AWS | Inherited by AWS. |
| MP | MP.L2-3.8.2 | Media Access | AWS | |
| MP | MP.L1-3.8.3 | Media Disposal | AWS | |
| MP | MP.L2-3.8.4 | Media Markings | AWS | |
| MP | MP.L2-3.8.5 | Media Accountability | AWS | |
| MP | MP.L2-3.8.6 | Portable Storage Encryption | AWS | |
| MP | MP.L2-3.8.7 | Removable Media | AWS | |
| MP | MP.L2-3.8.8 | Shared Media | AWS | |
| MP | MP.L2-3.8.9 | Protect Backups | AWS | |
| PE | PE.L1-3.10.1 | Limit Physical Access | AWS | AWS Inherited by AWS. |
| PE | PE.L2-3.10.2 | Monitor Facility | AWS | |
| PE | PE.L1-3.10.3 | Escort Visitors | AWS | |
| PE | PE.L1-3.10.4 | Physical Access Logs | AWS | |
| PE | PE.L1-3.10.5 | Manage Physical Access | AWS | |
| PE | PE.L2-3.10.6 | Alternative Work Sites | AWS | |
| SC | SC.L2-3.13.2 | Security Engineering | Istari Digital | Istari Digital manages the software development lifecycle pipelines which includes various security controls and tests that are implemented. |
Hybrid Controls
Hybrid controls involve shared responsibilities. These controls require a combination of approaches between Istari Digital and the tenant customer to implement specific aspects of the security control. For example, while Istari Digital may enable authentication features of the application, the customer may be responsible for assuring notification processes for when a user needs to be deleted or disabled. Hybrid controls involve network security configurations, encryption key management, and operating system patches and updates for the host infrastructure.
| Domain | Control | Control Title | Implementation Status | Implementation Narrative |
|---|---|---|---|---|
| AC | AC.L1-3.1.1 | Authorized Access Control | Hybrid | The Istari Digital Platform implements identity and access management controls using Zitadel (Identity) and Spice DB (Authorization) locally to the Control Plane. These controls are appropriately handled through role-based controls that can be incrementally adjusted per model within the platform. Identification of access procedures to the platform and the environment it resides will need to be documented for the platform in conjunction with a System Security Plan (SSP) to meet the threshold of this control. |
| AC | AC.L2-3.1.3 | Control CUI Flow | Hybrid | The Istari Digital Platform restricts system services from accessing data in a manner that could potentially expose the protected models. With the use of single use/signed URLs and various encryption methods, protected models can only be accessed by approved tools and services within the Data Plane. This is also limited to authorized end users of the platform. |
| AC | AC.L2-3.1.10 | Session Lock | Hybrid | Istari Digital requires and enforces automated session locks on all employee devices before granting access to protected systems. The customer is responsible for adjusting the control settings within their own systems. |
| AT | AT.L2-3.2.1 | Role-based Risk Awareness | Hybrid | Recommendations for this control include all Defense and Industrial Base and Government users completing the following training or equivalent prior to receiving access to the Istari Digital Platform Environment. 1) Security Awareness 2) CUI 3) Insider Threat While Istari Digital maintains its own acceptable use and training policy consistent with the above recommendations, the customer is responsible for controlling access and maintaining training requirements. |
| AT | AT.L2-3.2.2 | Role-based Training | Hybrid | In addition to the recommendation of AT.L2-3.2.1, privileged users with access to the Istari Digital Platform or the environment in which the platform is housed must complete specific security and compliance training suitable for their roles. |
| AT | AT.L2-3.2.3 | Insider Threat Awareness | Hybrid | The recommendation for this training is included with the Implementation Narrative of AT.L2-3.2.1. |
| CM | CM.L2-3.4.6 | Least Functionality | Hybrid | Istari Digital continually ensures that native systems and services operate with only the minimum functionality required to effectively complete authorized and necessary actions. Additional configurations may be required based on requirements of the customer environment to limit nonessential actions and enforce the principle of least privilege. |
| CM | CM.L2-3.4.7 | Nonessential Functionality | Hybrid | |
| CM | CM.L2-3.4.8 | Application Execution Policy | Hybrid | |
| IA | IA.L1-3.5.1 | Identification | Hybrid | The Istari Platform implements identity and access management controls using Zitadel. |
| IA | IA.L1-3.5.2 | Authentication | Hybrid | The Istari Digital Platform supports the use of Multi-Factor Authentication (MFA). |
| IA | IA.L2-3.5.3 | Multifactor Authentication | Hybrid | |
| IA | IA.L2-3.5.4 | Replay-Resistant Authentication | Hybrid | Authentication is handled with a combination of a single use session token and the credentialing hash. Both components are required for an authenticated request. |
| IR | IR-L2-3.6.1 | Incident Handling | Hybrid | Istari Digital has established an operational incident-handling capability for its systems, which includes preparation, analysis, containment, and recovery activities. We also identify vulnerabilities in the software development pipeline and communicate any appropriate patches. The customer's responsibility will lie within responding to their environment, tracking, documenting, reporting incidents internally, and communicating them between organizations if necessary. |
| IR | IR-L2-3.6.2 | Incident Reporting | Hybrid | |
| IR | IR-L2-3.6.3 | Incident Response Testing | Hybrid | |
| PS | PS.L2-3.9.1 | Screen Individuals | Hybrid | Istari Digital currently implements an onboarding/offboarding system that includes personnel screening, background checks and certification of appropriate citizenship status. This is maintained for as long as access is required. Istari Digital customers are responsible for implementing their own process to screen individuals that have access to the Istari Platform. |
| PS | PS.L2-3.9.2 | Personnel Actions | Hybrid | |
| SC | SC.L2-3.13.3 | Role Separation | Hybrid | Istari Digital has configured the platform for user functionality and system management to be identified through two different authentication pipelines. Istari Digital customers are responsible for implementing their user base to utilize those mechanisms. |
| SC | SC.L2-3.13.4 | Shared Resource Control | Hybrid | The Istari Digital Platform has several protections within its internal boundary. Additional protections are leveraged using separate VPCs for the Data and Control Planes. |
| SC | SC.L2-3.13.8 | Data in Transit | Hybrid | Data is encrypted in Transit using appropriate cryptography IAW FIP 140-3. |
| SC | SC.L2-3.13.11 | CUI Encryption | Hybrid | Cryptography is leveraged throughout the Istari Digital Platform to maintain confidentiality of the system. |
| SC | SC.L2-3.13.13 | Mobile Code | Hybrid | The Istari Digital Platform leverages customer infrastructure to enable digital threading. Customers are responsible for configuration of their infrastructure to limit the use of mobile code. |
| SC | SC.L2-3.13.15 | Communications Authenticity | Hybrid | Session management is implemented through multiple controls including Zitadel Reauthentication and Secure Sockets Layer (SSL). |
| SC | SC.L2-3.13.16 | Data at Rest | Hybrid | The Istari Digital Platform supports Data at Rest Encryption. The customer is responsible for ensuring organizational key management is in place to leverage this capability. |
| SI | SI-L1-3.14.1 | Flaw Remediation | Hybrid | Istari Digital conducts periodic risk and vulnerability assessments as a part of its software development lifecycle. If a vulnerability is identified, an appropriate notification will be provided to all relevant stakeholders in a timely manner to inform decision of risk. Environment monitoring of other software and tools will also need to be conducted. |
| SI | SI-L1-3.14.2 | Malicious Code Protection | Customer | Istari Digital maintains malicious code protection within the backend of the platform. Customers are responsible for ensuring their systems have the same protection and that the data they process through the Istari Platform is safe. |
| SI | SI-L2-3.14.3 | Security Alerts & Advisories | Customer | Istari Digital does receive security alerts and advisories as is appropriate to its operations. If Istari Digital software is affected appropriate notification pipelines will be initiated and the customer will be informed as necessary. |
| SI | SI-L1-3.14.4 | Update Malicious Code Protection | Customer | Istari Digital maintains malicious code protection within the backend of the platform. Customers are responsible for ensuring their systems have the same protection and that the data they process through the Istari Platform is safe. |
| SI | SI-L1-3.14.5 | System & File Scanning | Customer | |
| SI | SI-L2-3.14.6 | Monitor Communications for Attacks | Customer | Istari Digital has a comprehensive monitoring program in the environment. |
| SI | SI-L2-3.14.7 | Identify Unauthorized Use | Customer |
Customer Controls
The remaining controls for CMMC are entirely client responsibility. They include securing customer data, customer tenant environments, client-side data encryption and integrity, and the security of customer-created or managed applications. The customer must implement these controls to ensure their data is appropriately protected.
| Domain | Control | Control Title | Implementation Status | Implementation Narrative |
|---|---|---|---|---|
| AC | AC.L1-3.1.2 | Transaction & Function Control | Customer | The customer is responsible for who has access to the actions and data that will be processed through the Istari Platform. |
| AC | AC.L2-3.1.4 | Separation of Duties | Customer | Separation of duties and least privilege will need to be configured in multiple places within the environment during the deployment process. Primary Considerations for this control include IAM (AWS) and administrative accounts in the VMs. |
| AC | AC.L2-3.1.5 | Least Privilege | Customer | |
| AC | AC.L2-3.1.6 | Non-Privilege Account Use | Customer | |
| AC | AC.L2-3.1.7 | Privileged Functions | Customer | |
| AC | AC.L2-3.1.8 | Unsuccessful Logon Attempts | Customer | Through Zitadel the Istari Digital Platform can integrate with various identity providers, through which unsuccessful logon attempts will be handled and may require some configuration to meet this threshold. |
| AC | AC.L2-3.1.11 | Session Termination | Customer | This can be configured in multiple places in the environment. On existing deployments, Istari Digital has implemented this in a Virtual Private Network (VPN), the Customer identity and access management (CIAM) supported by Zitadel, and the Identity and Access Management (IAM) supported by AWS. |
| AC | AC.L2-3.1.12 | Control Remote Access | Customer | Remote connections will need to be managed in a way to prevent when communicating with external systems. Istari Digital has implemented this control through the use of a VPN (Pritunl) in current deployments; however, customers retain the flexibility to choose their preferred VPN. |
| AC | AC.L2-3.1.13 | Remote Access Confidentiality | Customer | |
| AC | AC.L2-3.1.14 | Remote Access Routing | Customer | |
| AC | AC.L2-3.1.15 | Privileged Remote Access | Customer | |
| AC | AC.L2-3.1.16 | Wireless Access Authorization | Customer | No wireless access points exist within the defined system boundary. |
| AC | AC.L2-3.1.17 | Wireless Access Protection | Customer | No wireless access points exist within the defined system boundary. |
| AC | AC.L2-3.1.18 | Mobile Device Connection | Customer | No mobile devices exist within the defined system boundary. |
| AC | AC.L2-3.1.19 | Encrypt CUI on mobile | Customer | No mobile devices exist within the defined system boundary. |
| AC | AC.L2-3.1.20 | External Connections | Customer | No external dependencies exist within the defined system boundary. |
| AC | AC.L2-3.1.21 | Portable Storage Use | Customer | No portable storage devices exist within the defined system boundary. |
| AC | AC.L2-3.1.22 | Control Public Information | Customer | No public facing access points exist within the defined system boundary. |
| AU | AU-L2-3.3.1 | System Auditing | Customer | Istari Digital will support the aggregation of logs with platform features that allow capturing audit records at various levels of abstraction, including details such as timestamps, event descriptions, user identifiers, and other necessary event details. Maintenance and review of the logs will need to be maintained to further support compliance in this area. |
| AU | AU-L2-3.3.2 | User Accountability | Customer | |
| AU | AU-L2-3.3.3 | Event Review | Customer | |
| AU | AU-L2-3.3.4 | Audit Failure Alerting | Customer | |
| AU | AU-L2-3.3.5 | Audit Correlation | Customer | |
| AU | AU-L2-3.3.6 | Reduction & Reporting | Customer | |
| AU | AU-L2-3.3.7 | Authoritative Time Source | Customer | |
| AU | AU-L2-3.3.8 | Audit Protection | Customer | |
| AU | AU-L2-3.3.9 | Audit Management | Customer | |
| CA | CA.L2-3.12.1 | Security Control Assessment | Customer | Periodic assessment will need to occur on the environment, ensuring awareness of the defined security requirements and that your systems operate in environments that complement our security controls. Additionally, the system security plans, reports, and maintenance will need to be updated, addressing any highlighted weaknesses or vulnerabilities for platform environments. |
| CA | CA.L2-3.12.2 | Plan of Action and Milestones | Customer | |
| CA | CA.L2-3.12.3 | Security Control Monitoring | Customer | |
| CA | CA.L2-3.12.4 | System Security Plan | Customer | |
| CM | CM.L2-3.4.3 | System Change Management | Customer | Istari Digital offers documentation on platform and configuration updates, facilitating informed approval for system changes. |
| CM | CM.L2-3.4.4 | Security Impact Analysis | Customer | |
| CM | CM.L2-3.4.5 | Access Restrictions for Change | Customer | |
| CM | CM.L2-3.4.9 | User-Installed Software | Customer | |
| IA | IA.L2-3.5.6 | Identifier Handling | Customer | The Istari Digital Platform supports the use of an external identity provider. This functionality will need to be configured either with the external provider or another tool. |
| IA | IA.L2-3.5.7 | Password Complexity | Customer | The Istari Digital Platform supports the use of an external identity provider. This functionality will need to be configured either with the external provider or another tool. |
| IA | IA.L2-3.5.8 | Password Reuse | Customer | The Istari Digital Platform supports the use of an external identity provider. This functionality will need to be configured either with the external provider or another tool. |
| IA | IA.L2-3.5.9 | Temporary Passwords | Customer | The Istari Digital Platform supports the use of temporary passwords for the purposes of account creation. |
| RA | RA.L2-3.11.1 | Risk Assessments | Customer | Istari Digital conducts periodic risk assessments as a part of its software development lifecycle. If a vulnerability is identified, an appropriate notification will be provided to all relevant stakeholders to inform the decision of risk. Risk assessment will need to be conducted periodically on the environment, including any relevant scanning of the environment. |
| RA | RA.L2-3.11.2 | Vulnerability Scan | Customer | |
| RA | RA.L2-3.11.3 | Vulnerability Remediation | Customer | |
| SC | SC.L1-3.13.1 | Boundary Protection | Customer | Boundary protections and configurations will need to occur to appropriately protect the environment. |
| SC | SC.L1-3.13.5 | Public-Access System Separation | Customer | No public access points exist within the defined system boundary. |
| SC | SC.L2-3.13.6 | Network Communication by Exception | Customer | Configuration of the environment will be required to implement these boundary protections. |
| SC | SC.L2-3.13.7 | Split Tunneling | Customer | |
| SC | SC.L2-3.13.9 | Connections Termination | Customer | Configuration to support this control will be required. |
| SC | SC.L2-3.13.10 | Key Management | Customer | A service such as Key Management Service (KMS) will need to be actively used to maintain keys to support compliant cryptography. |
| SC | SC.L2-3.13.12 | Collaborative Device Control | Customer | No collaborative computing devices exist within the defined system boundary. |
| SC | SC.L2-3.13.14 | Voice over Internet Protocol (VoIP) | Customer | No VoIP devices exist within the defined system boundary. |