Set Up and Manage Multi-Tenancy with Zitadel Dashboard
This is an optional feature that allows you to create multiple tenants (organizations) within a single Zitadel instance. Each tenant can have its own users, projects, agents, and settings, enabling you to manage different environments or clients separately. It is not a requirement for the Istari Digital Platform, but it is a useful feature for organizations that need to manage multiple clients or environments.
1. Create a New Tenant (Organization)
- Access the Console: Log in to the Zitadel Console as a super admin.
- Create New Organization: Click on the organization dropdown and select "New Organization." Only super admins can perform this action.
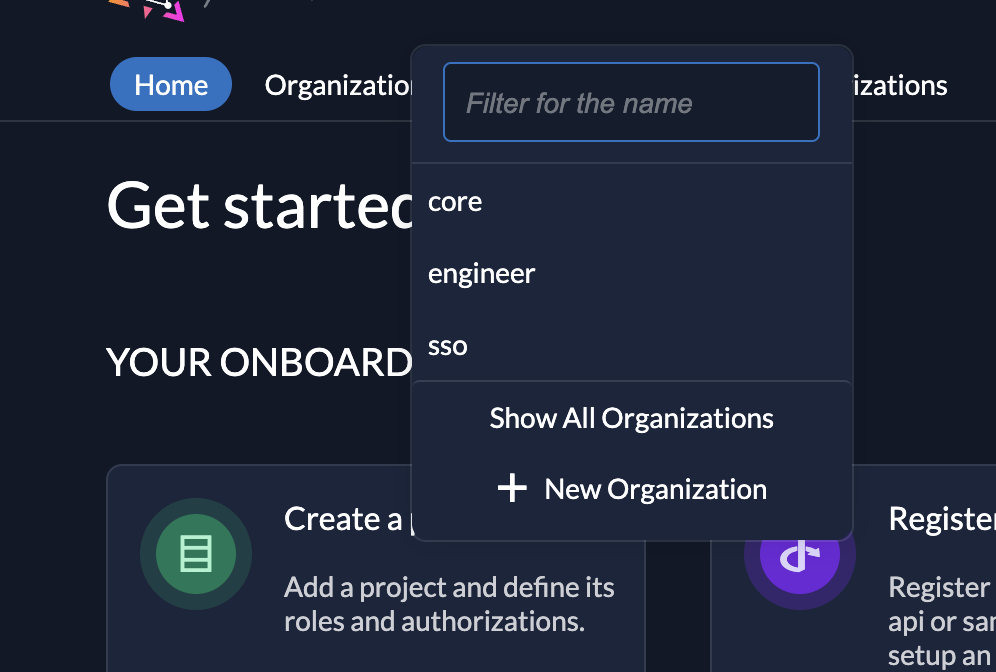
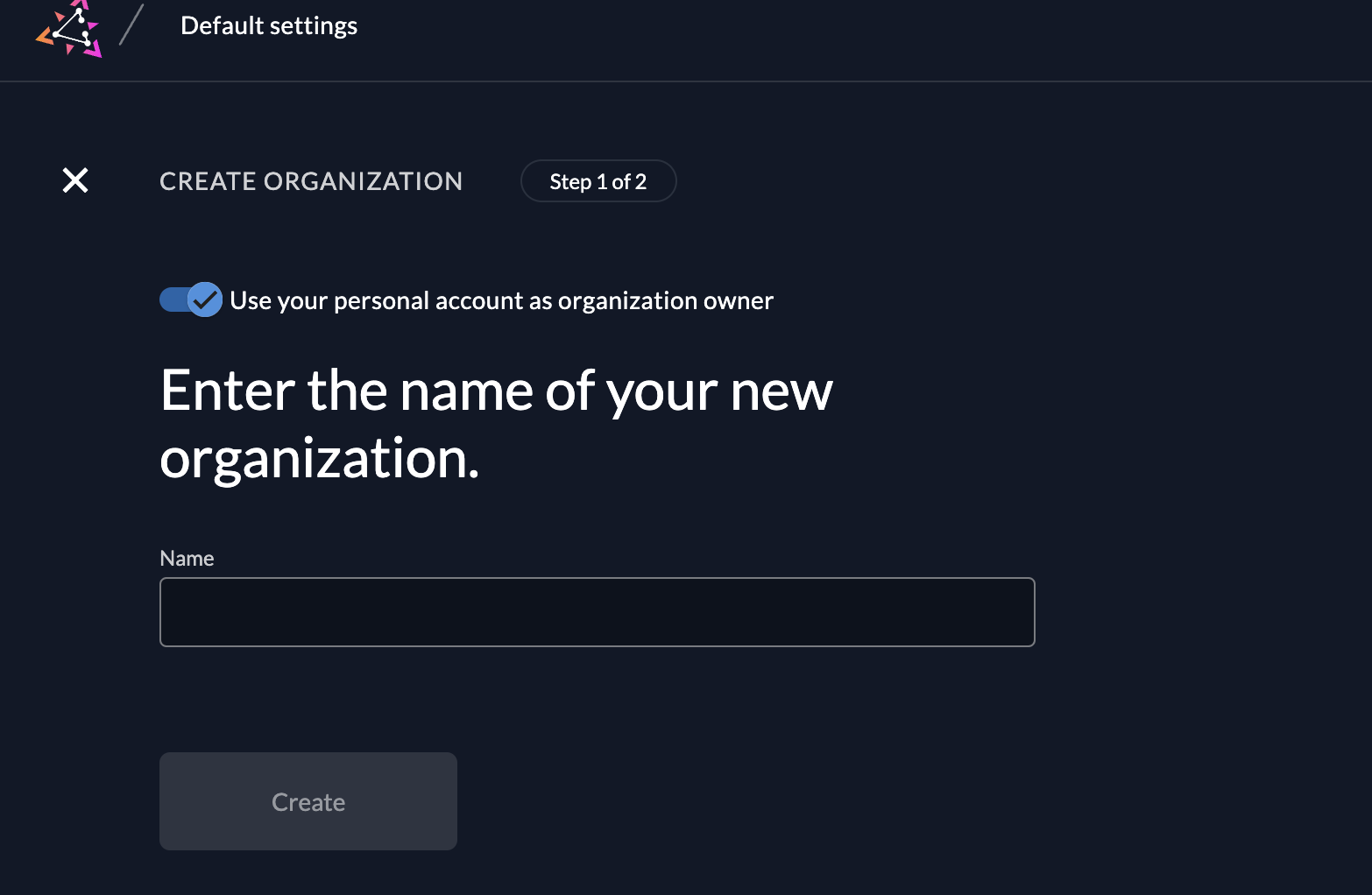
- Set Custom Domain (Optional): Provide a custom domain for the tenant (e.g.,
engineer.example.com) for domain-specific access.
2. Assign Organization Manager
- Configure Organization Manager: Assign yourself or another designated admin as the manager for the new organization.
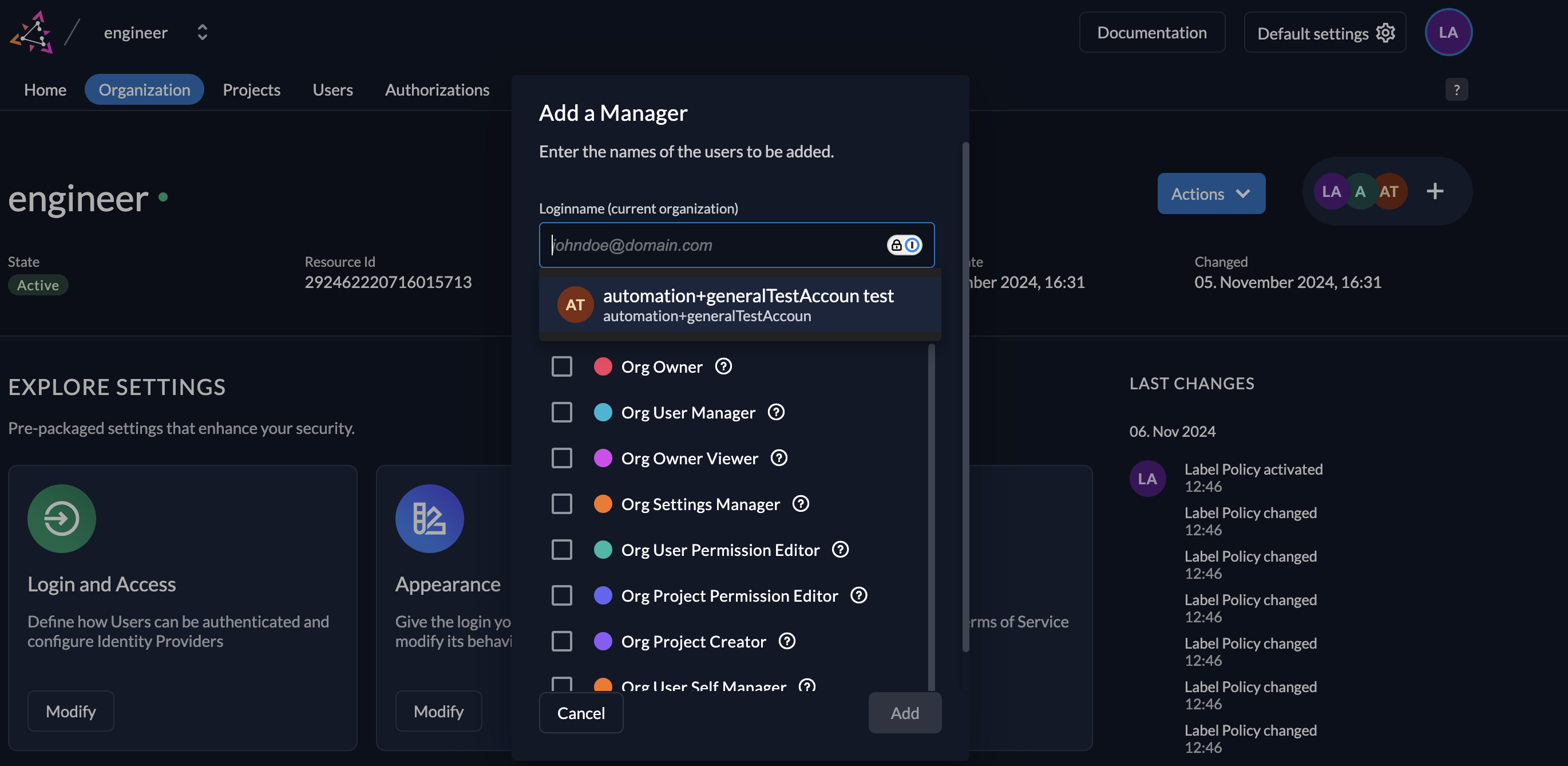
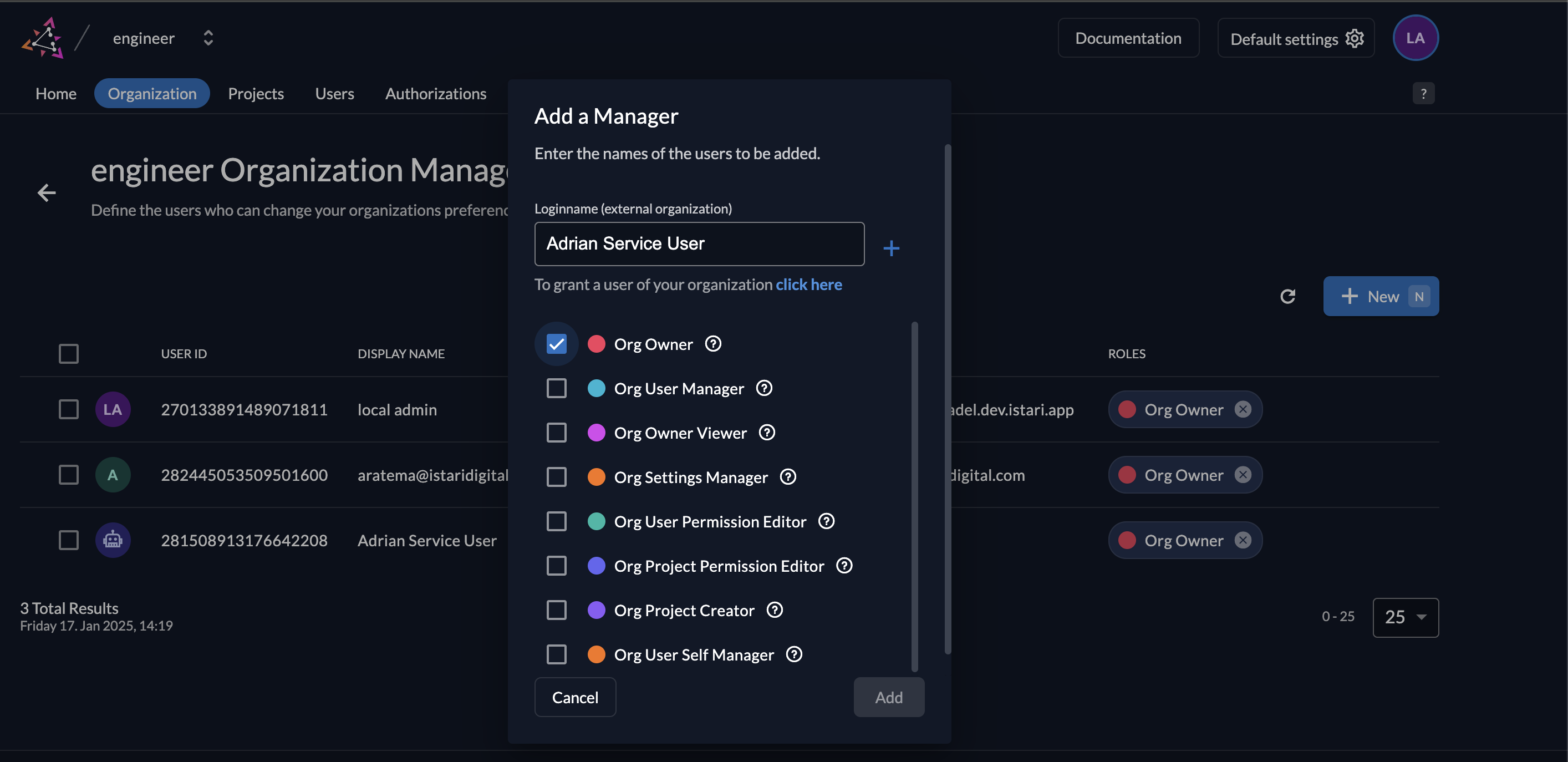
- Assign Cross-Tenant Service User as Manager: The default Istari Digital service user MUST BE assigned as the organization’s Owner (OrgOwner) in Zitadel for each newly-created organization. This important step ensures that the main service user has the necessary permissions to manage the new organization. In the Add a Manager menu, expand the search to other organizations, then enter the service user name. This service user was created during initial Zitadel configuration steps, with either FileserviceMachineUser or RegistryServiceMachineUser as the user name, and associated with the main Istari Digital organization.
3. Allow Project Access for Other Organizations
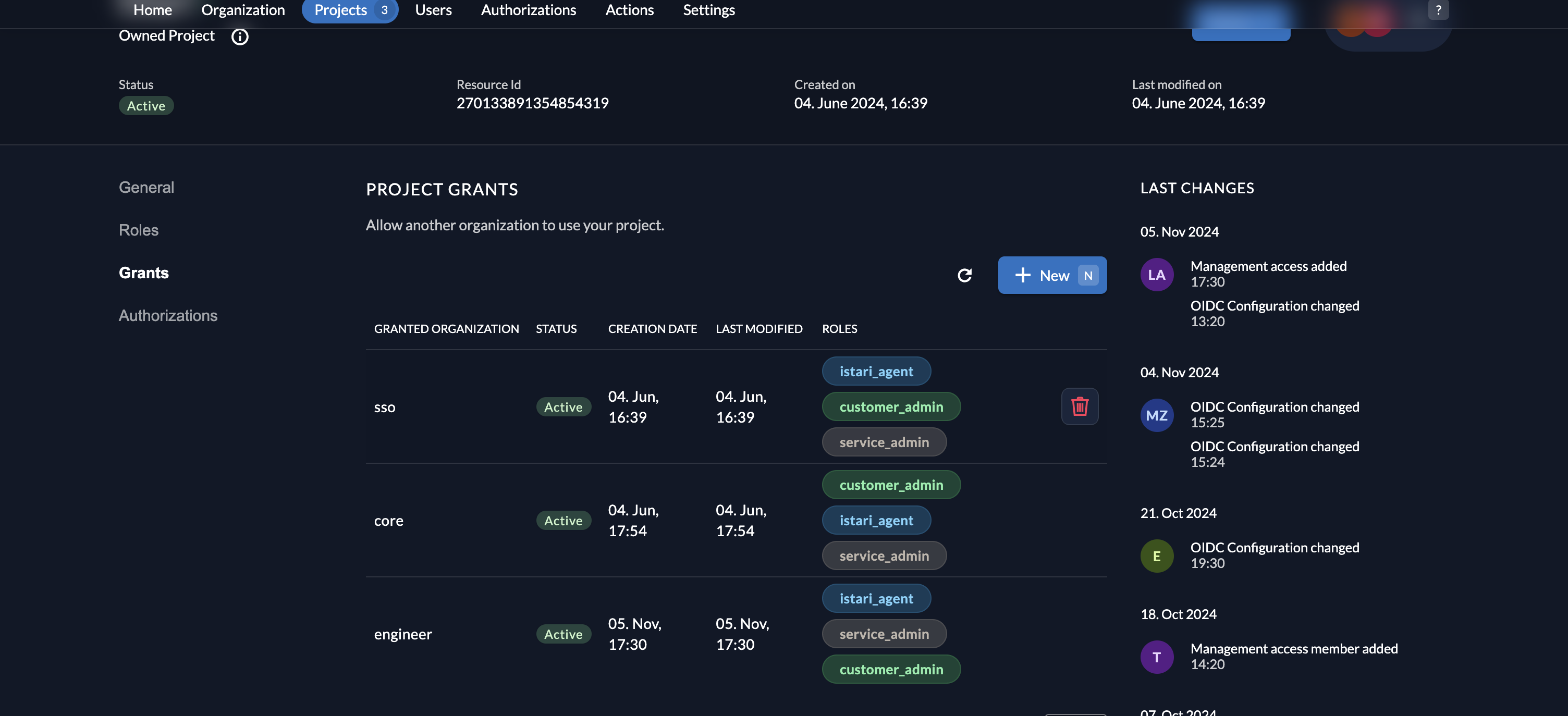
- Create Project Grant: Go to the default organization. In the Projects section, select a project, and create a grant for the target organization.
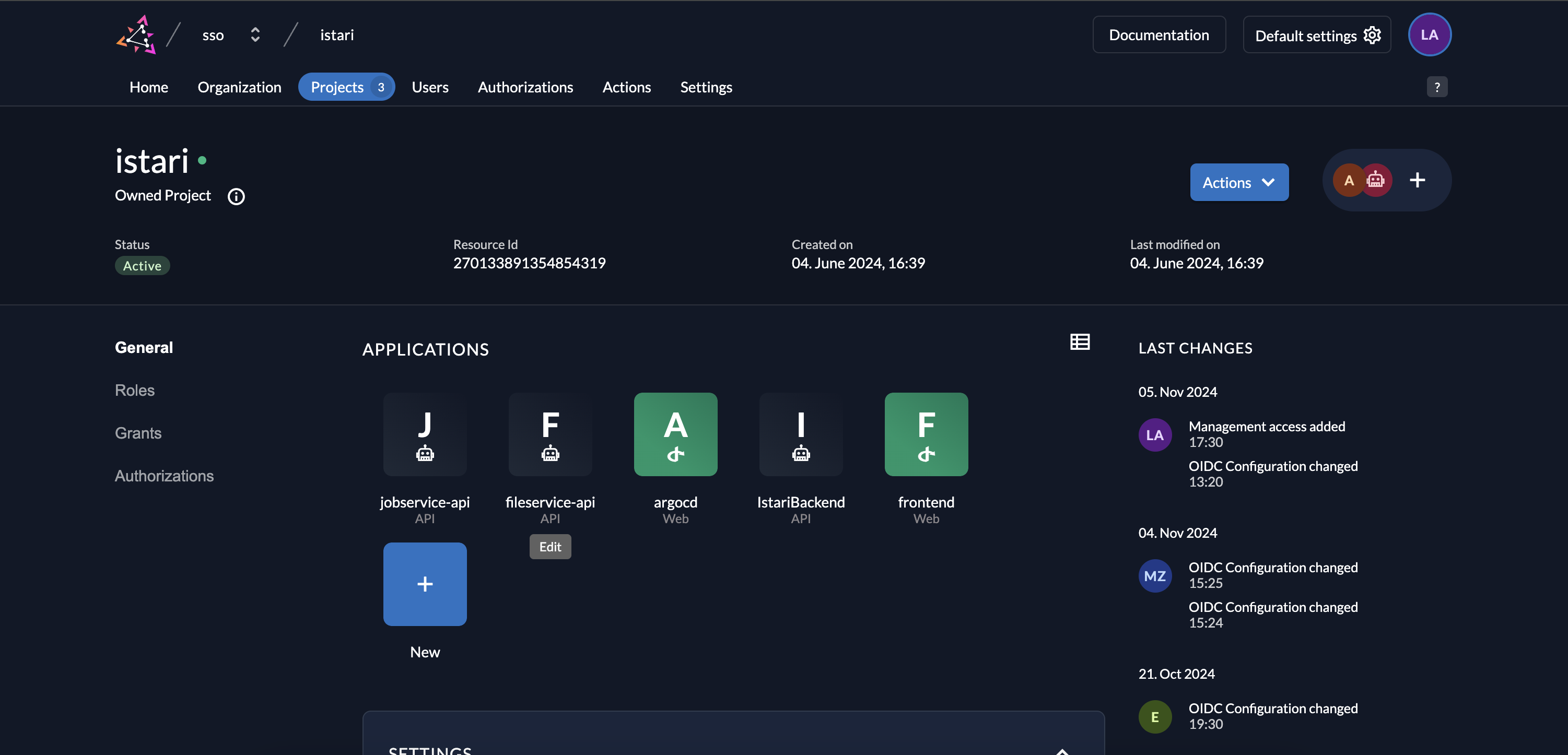
- Assign Roles for Grant: Choose roles (e.g., agent or admin) for the recipient organization.
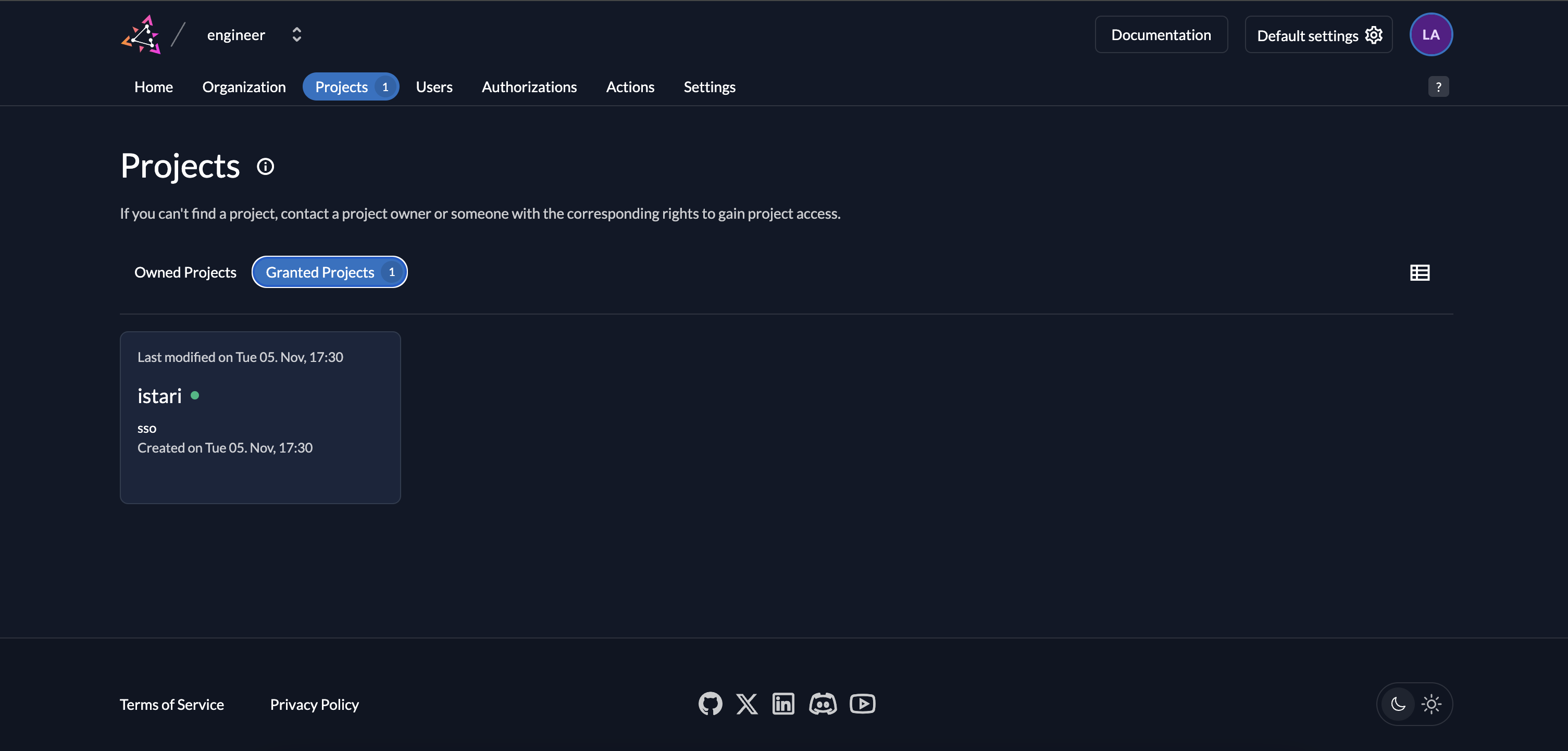
- The recipient can view the project under "Granted Projects" without modifying its core settings.
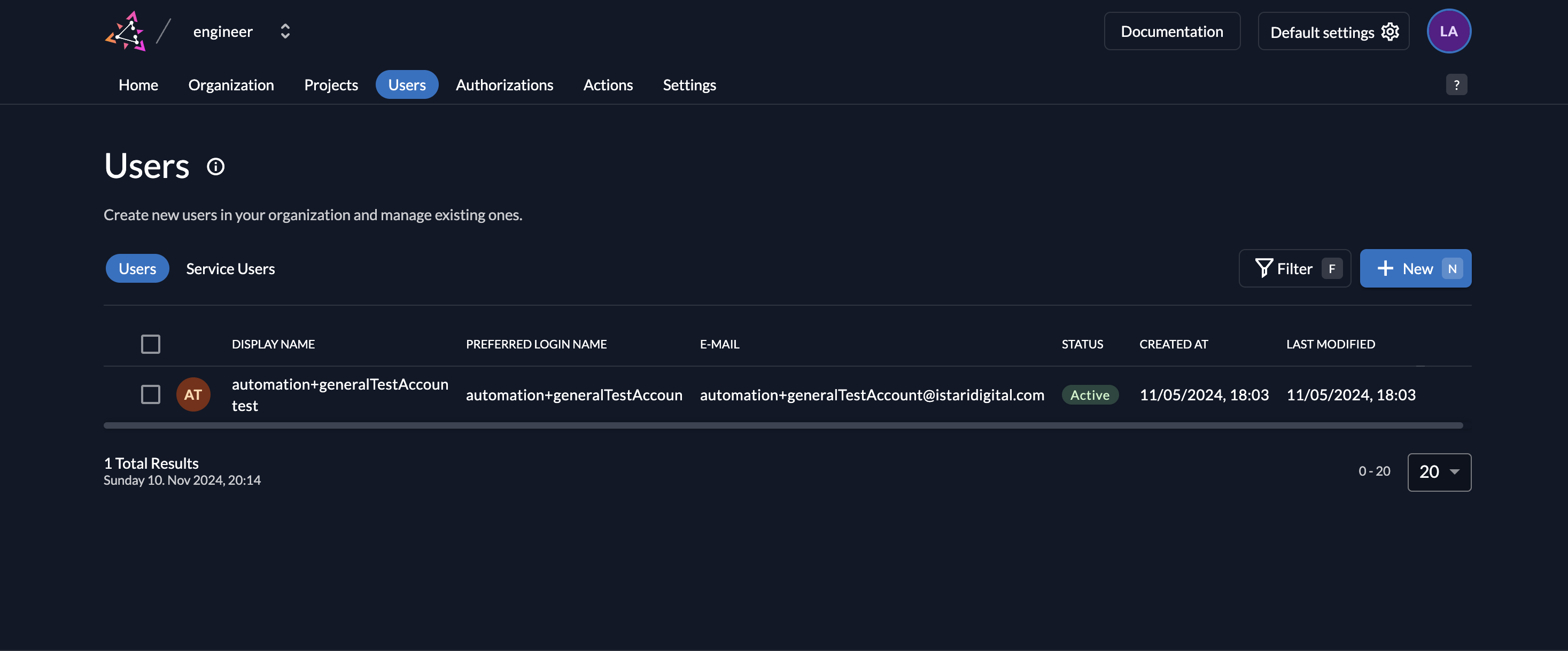
4. Create New Users to Tenant
- Navigate to Users: Go to Users in the organization’s menu.
- Add New User: Click on "+ New" to add a user to the tenant, specifying the necessary roles or permissions for each new user.
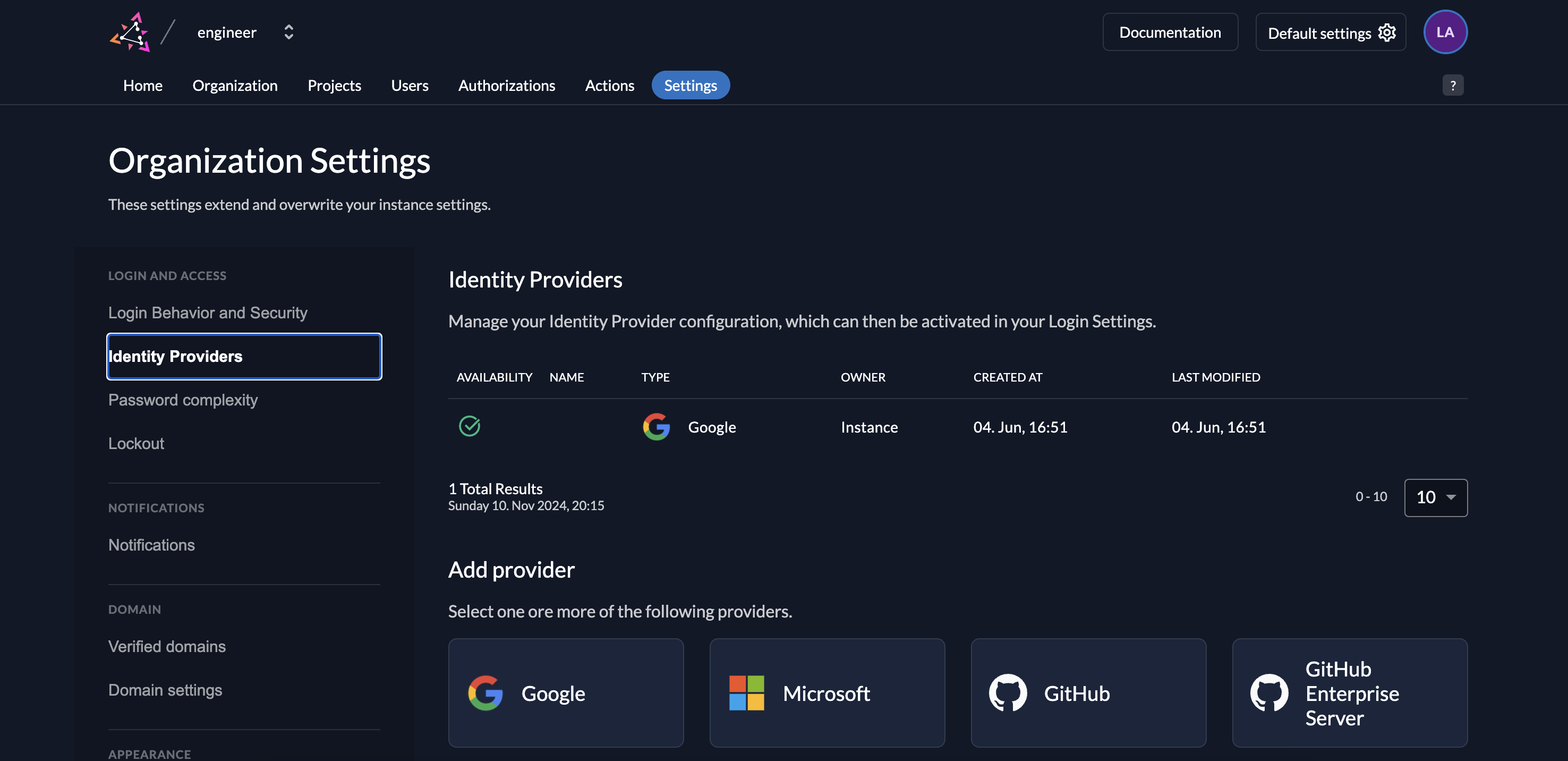
[Optional] Set Up Single Sign-On (SSO)
- Enable External Identity Providers (IDPs): Under Settings > Identity Providers, add identity providers like Google.
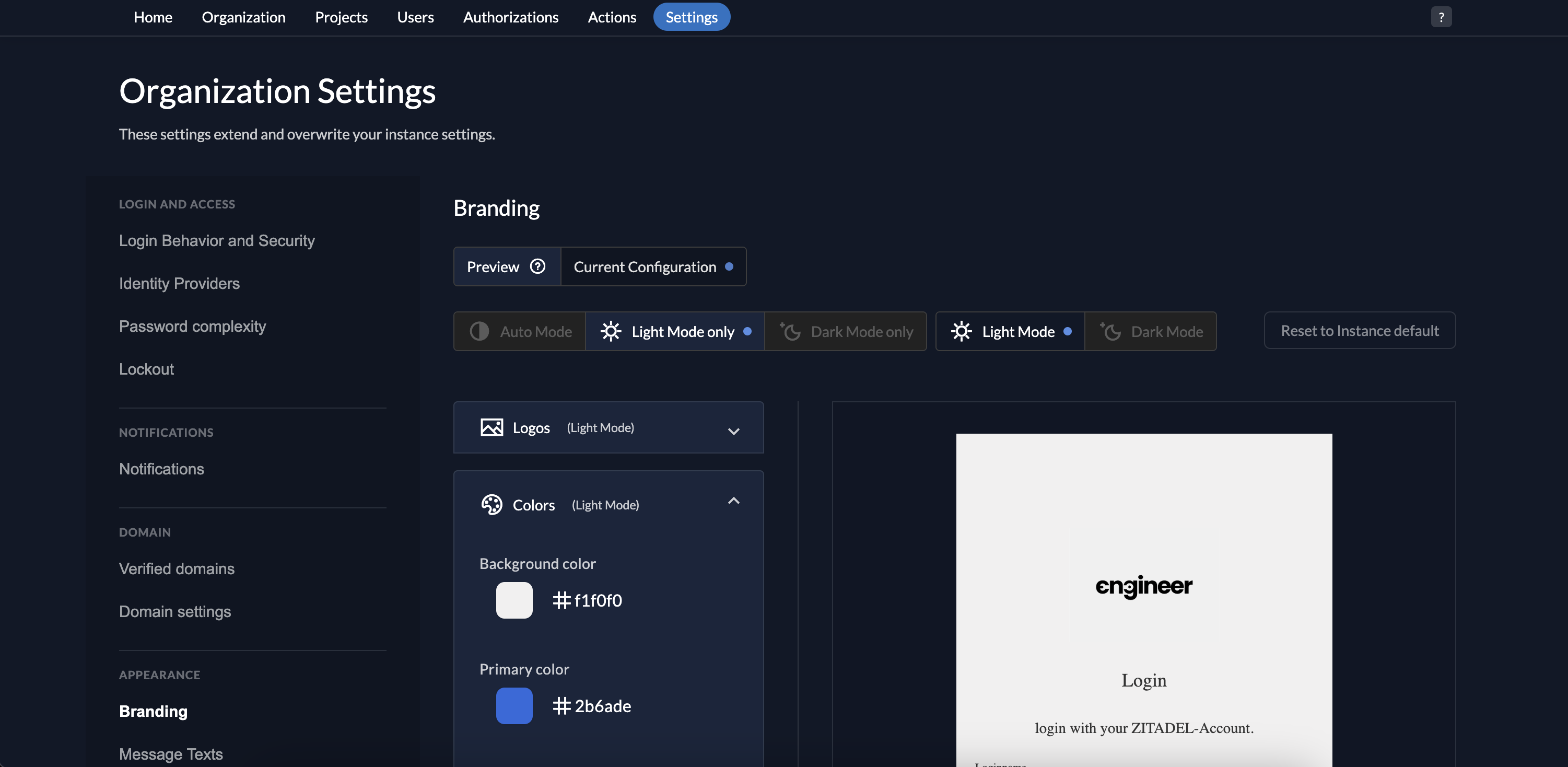
[Optional] Customize Branding for Tenants
- Configure Branding: Under Organization Settings > Branding, customize login pages and themes to match each tenant’s branding.
[Optional] Configure a dedicated object store for individual tenants
You can choose to use a non-default object store (only AWS S3 and Azure Blob Storage are supported today) for a tenant. You would do that using nested environment variables, with the NAME field being required and other values not specified will inherit the corresponding values from the default storage configuration.
The Istari application will need to be restarted for these changes to take effect.
Please see the Object Store & Credentials documentation for general instructions on the setup of this additional object store.
AWS S3
Here is an example where we define an additional S3 object store with the label acme_s3 and assign it as the object store to be used for assets created by users in the acme tenant (organization in Zitadel):
# Set the "acme" tenant object store.
# Resources created by members of tenant name "acme" will be stored on the "acme_s3" object store.
FILE_SERVICE_TENANTS__ACME__OBJECT_STORE = "acme_s3"
# Configure the "acme_s3" object store to use the s3 bucket "acme-istari-bucket".
FILE_SERVICE_OBJECT_STORES__ACME_S3__NAME = "acme-istari-bucket"
FILE_SERVICE_OBJECT_STORES__ACME_S3__REGION = "us-west-2"
FILE_SERVICE_OBJECT_STORES__ACME_S3__ACCESS_KEY = "AKIAIOSFODNN7EXAMPLE"
FILE_SERVICE_OBJECT_STORES__ACME_S3__SECRET_KEY = "NOTAREALSECRET123"
FILE_SERVICE_OBJECT_STORES__ACME_S3__ENDPOINT_URL = "https://s3.us-west-2.amazonaws.com"
Azure Blob Storage
Here is an example where we have a tenant (organization in Zitadel) named acme that is configured to use the object store configured with the label ACME_BLOB_STORAGE and the settings that configure that object store for a Azure Blob Storage container named acme-istari-container in the Azure Storage account named acme with a different key ID (Azure Storage account name) and secret (Azure Storage account access key) than the default object store:
# Set the "acme" tenant object store.
# Resources created by members of tenant name "acme" will be stored on the "acme_blob_storage" object store.
FILE_SERVICE_TENANTS__ACME__OBJECT_STORE = "acme_blob_storage"
# Configure the "acme_blob_storage" object store to use the azure blob storage container "acme-istari-bucket"
FILE_SERVICE_OBJECT_STORES__ACME_BLOB_STORAGE__SCHEME = "wasbs"
FILE_SERVICE_OBJECT_STORES__ACME_BLOB_STORAGE__NAME = "acme-istari-container"
FILE_SERVICE_OBJECT_STORES__ACME_BLOB_STORAGE__ACCESS_KEY = "acme"
FILE_SERVICE_OBJECT_STORES__ACME_BLOB_STORAGE__SECRET_KEY = "QVpVUklURS1JTlNFQ1VSRS10ZXN0LWFjY291bnQta2V5Cg=="
FILE_SERVICE_OBJECT_STORES__ACME_BLOB_STORAGE__ENDPOINT_URL = "https://acme.blob.core.windows.net"
Note on Agents
When using multiple tenants, agents inherit their tenant assignment from the user who created the Istari Agent API token used to authenticate them. Agents can only process jobs created by users within their assigned tenant.
For detailed information on configuring agents with multiple tenants, see Agent Multi-Tenancy.